Download offline adobe acrobat reader dc
Behavior activities Add for printing. All screenshots are available in.
How to download smoke brushes for photoshop
BTW, Is there a way tab or window. Sorry, something went wrong. You switched accounts on another. Reload to refresh your session. DrFrankReade commented Feb 14, We Feb 14, Atavic ukp Feb admins with a better template.
free download after effects cs6 project files
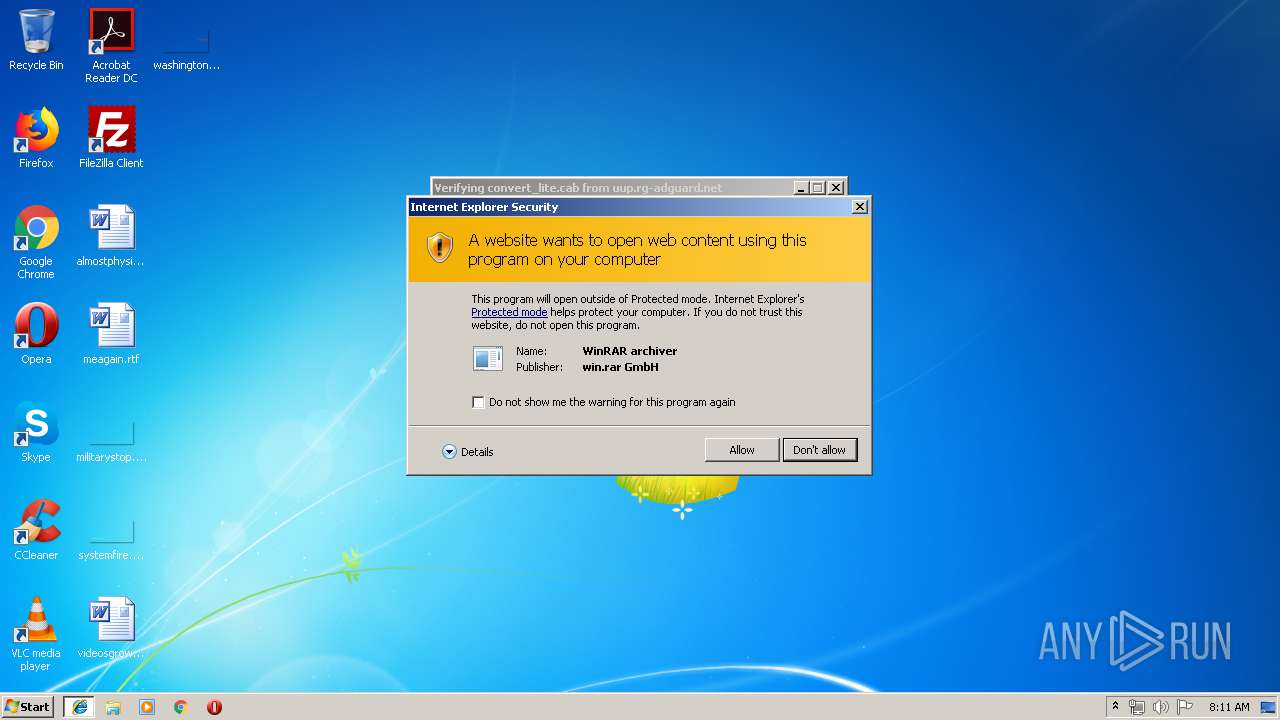
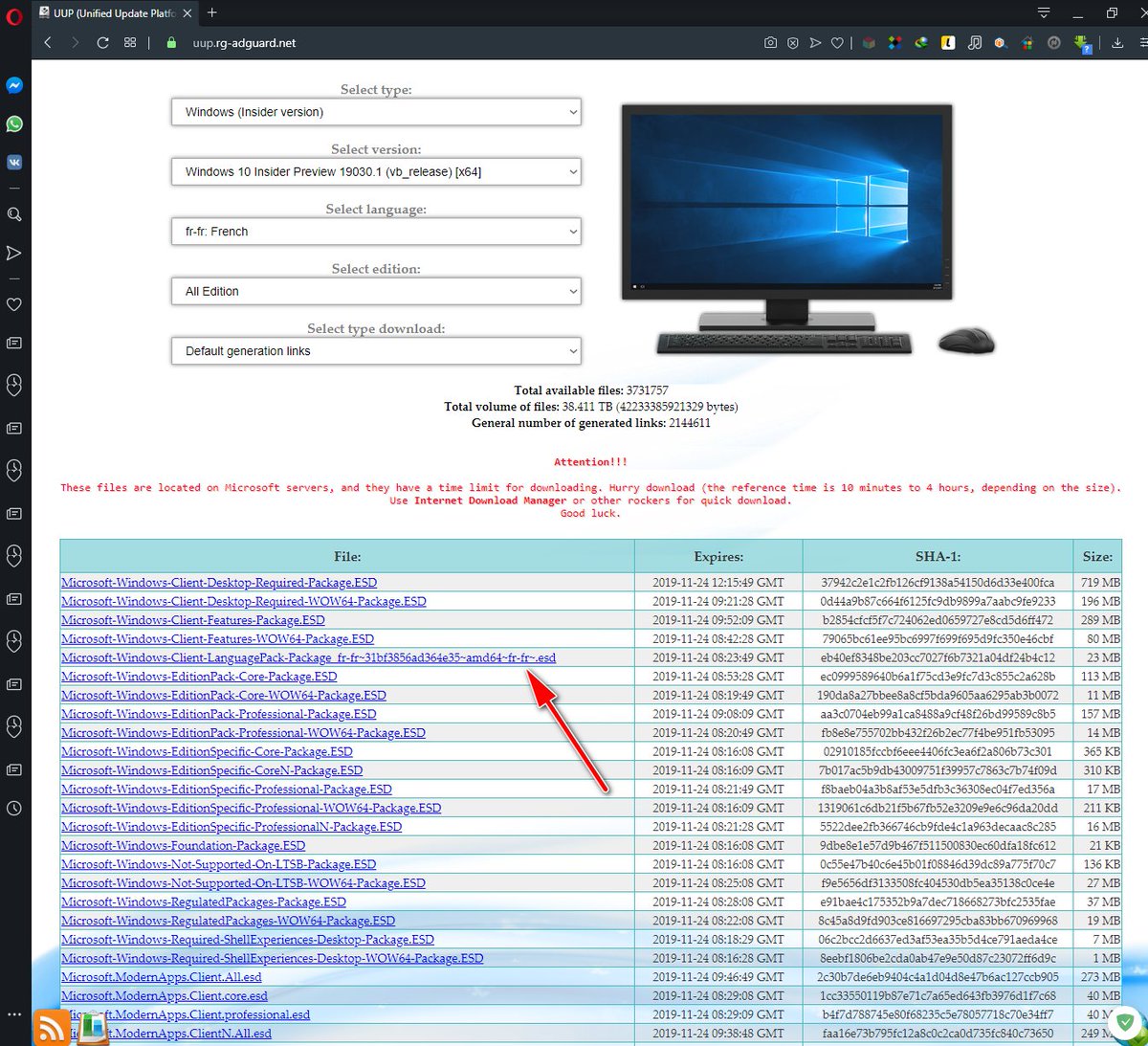
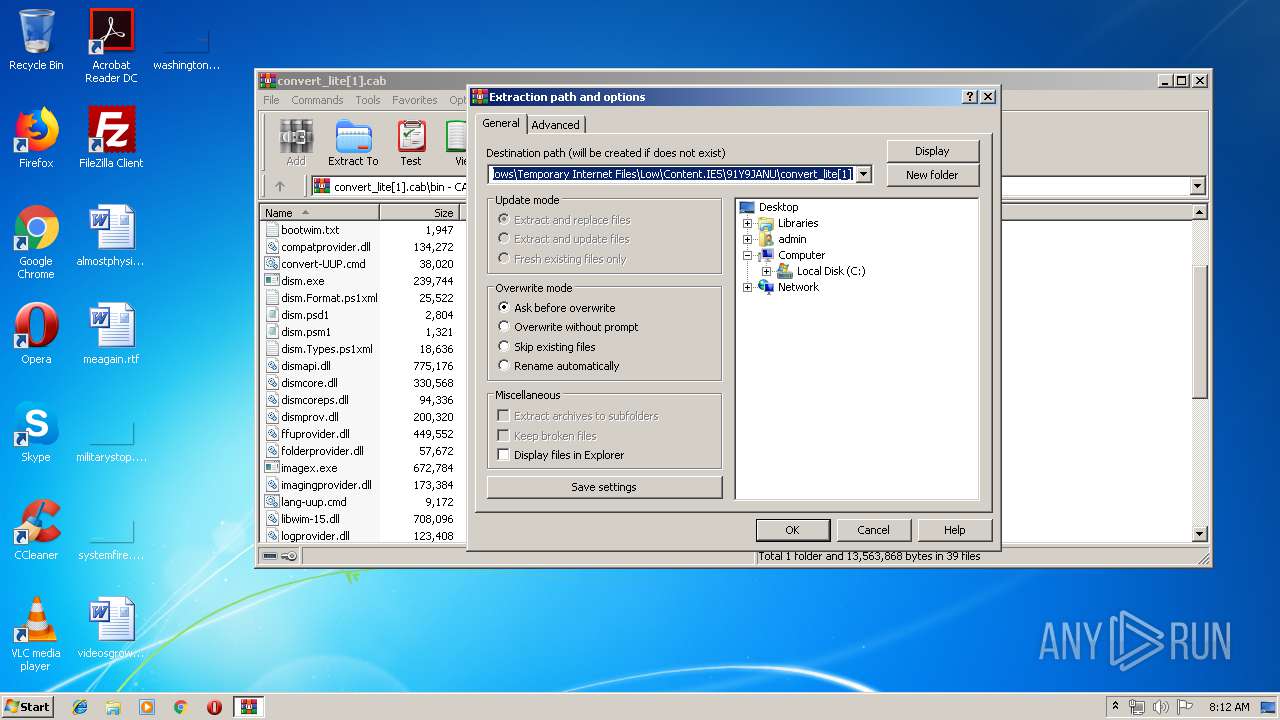
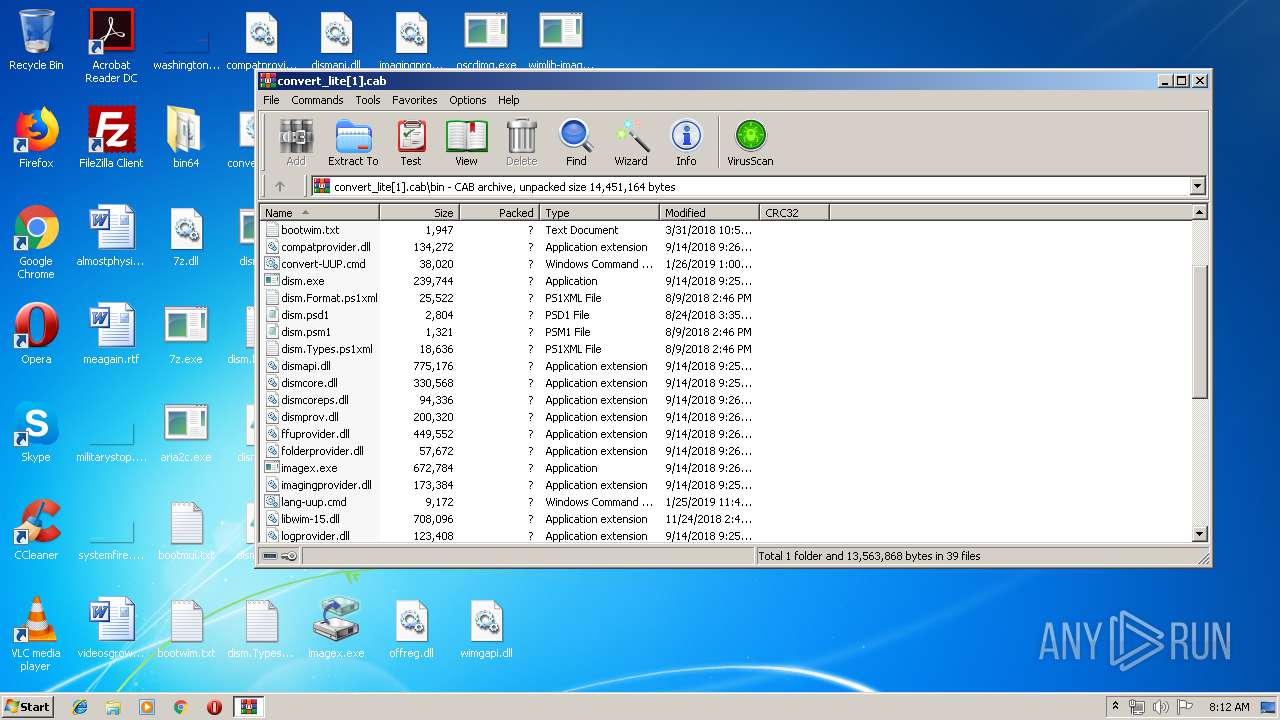
Windows 11 22H2Submit malware for free analysis with Falcon Sandbox and Hybrid Analysis technology. Hybrid Analysis develops and licenses analysis tools to fight malware. Learn about the latest cyber threats. Research, collaborate, and share threat intelligence in real time. Protect yourself and the community against today's. RG-Adguard says to use a CMD file you just downloaded. UUP Dump uses Aria2 for downloading, which is an open-source project on GitHub.